A malware sent via email infecting a company, all because of an employee’s negligence: this is the typical scenario that security managers are faced with, according to Cisco’s 2019 CISO Benchmark Report. In order to prevent breaches, CISOs focus in particular on integrating security into all their internal processes, into access management and human risk.
On which threats should Chief Information Security Officers (CISOs) focus their attention as a priority and what measures do they take to protect their business? The 2019 edition of Cisco’s CISO Benchmark Report addresses these issues and shows that CISOs are the ones most frequently dealing with malware and are implementing a set of additional practices to deal with the threats.
Emails: the main medium used for attacks
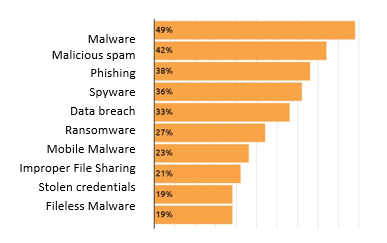
Malware and its variants (ransomware and spyware) are responsible for over half of the verified security breaches experienced by the 3200 IT security managers surveyed in the study. Emails also appear as a risk vector that needs to be closely monitored, malicious spam and phishing attempts being involved in one in four breaches. As a result, user behavior is now CISOs’ highest concern. In comparison, the risks associated with switching to the cloud seem easier to control.
From product acquisition to access rights, security is everywhere
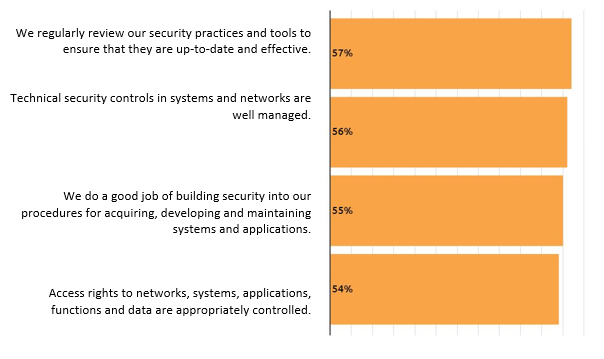
CISOs regularly review their security practices and tools to safeguard their organizations. They ensure that technical controls are properly managed and build security into their procedures for acquiring, developing and maintaining systems and applications. In addition, access rights to networks, systems, applications, functions and data should be appropriately controlled. Respondents also believe that they do a good job of building security into systems and applications.
More than half of the security managers also believe that they are doing an “excellent job” of managing human resources security through employee onboarding and good processes for handling employee transfers and departures On the other hand, less than half of the CISOs think they do a good job building security into external and customer-facing mobile applications.
Download the report
What type of security incidents/attacks were you faced with in the last year?
The 4 additional most used practices employed by CISOs to safeguard the organization